- Tracking users and their permissions
- Providing a catalog of available services with their API endpoints
In essence, Keystone is to provide authentication and authorization function for the various elements in OpenStack. User presents a credential to Keystone and based on the result of the authentication process assign a role along with a token to the user. This role specifies the rights and/or privileges to perform different operations within OpenStack.
User can be a
- person
- service (e.g. Nova, Cinder, Neutron ...)
- end point (a network-accessible address such as a URL, RESTful API)
User can be grouped together as Tenant which can be a project, group or organization.
Keystone assigns a tenant and a role to a user. A user can have different roles in different tenants.
This diagram show the flow of an authentication process
image source: https://senecacd.files.wordpress.com/2012/11/identity-diagram.png
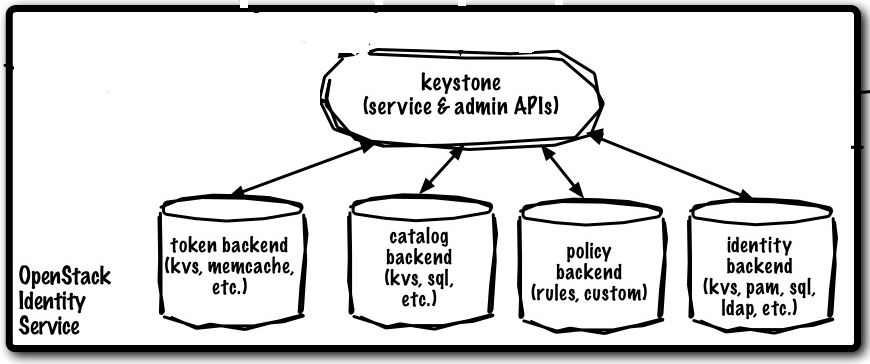
From the OpenStack Developer Guide, Keystone is organized as a group of internal services exposed on one or many endpoints. The internal services are:
Identity
- The Identity service provides auth credential validation and data about Users, Groups, Projects, Domains and Roles, as well as any associated metadata.
- In the basic case all this data is managed by the service, allowing the service to manage all the CRUD associated with the data.
- In other cases, this data is pulled, by varying degrees, from an authoritative backend service. An example of this would be when backending on LDAP. See LDAP Backend below for more details.
Token
- The Token service validates and manages Tokens used for authenticating requests once a user’s credentials have already been verified.
Catalog
- The Catalog service provides an endpoint registry used for endpoint discovery.
Policy
- The Policy service provides a rule-based authorization engine and the associated rule management interface.
image source: http://allthingsopendotcom.files.wordpress.com/2014/07/keystone.png
Each of these internal services can be configured to use a service back-end. IBM has a good article explaining the components of Keystone in which it outlines some of the more common back ends include:
- Key Value Store. An interface supporting primary key lookups, such as an in-memory dictionary.
- Memcached. Distributed memory caching system
- Structured Query Language (SQL). Uses SQLAlchemy (a Python SQL toolkit and Object Relational Mapper) to store data persistently
- Pluggable Authentication Module (PAM). Uses the local system's PAM service to authenticate
- Lightweight Directory Access Protocol (LDAP). Connects via the LDAP to a back-end directory, such as Active Directory®, to authenticate users and obtain role information
Lastly, as mentioned in my other port, one new feature for OpenStack Juno release is the federation of identity services. If you are interested take a look here. Instead of a single identity service,a wide range of identity services distributed around the Internet, called Identity Providers (IdPs). The advantages of using external identity providers are
numerous, and include:
- No need to provision user entries in Keystone, since the user entries already exist in the IdP's databases.
- No need to build additional authentication mechanisms into Keystone, since the IdPs take care of authenticating their own users using whichever technologies they deem to be appropriate. So multiple authentication technologies are already in use.
- No need to support users who forget their passwords. The IdPs already do this.
- Multiple collaborating organizations can quickly share the same cloud services by each one using their own local IdP to authenticate their users.
- Provides single sign on to the user, who can use the same set of credentials with his IdP to access many different services on the Internet.
Related Post:
OpenStack Series: Part 1: How do you look at OpenStack?
OpenStack Series: Part 2: What's new in Juno Release.
OpenStack Series: Part 4: Nova - Compute Service.
OpenStack Series: Part 5: Glance - Image Service
OpenStack Series: Part 6: Cinder - Block Storage Service
OpenStack Series: Part 7: Swift - Object Storage Service
OpenStack Series: Part 8: Neutron - Networking Service
OpenStack Series: Part 9: Horizon - a web based UI Service
OpenStack Series: Part 10: Heat - Orchestration Service
OpenStack Series: Part 11: Ceilometer - Monitoring and Metering Service
OpenStack Series: Part 12:Trove - Database Service
OpenStack Series: Part 13: Docker in OpenStack
OpenStack Series: Part 14: Sahara - Data Processing Service
OpenStack Series part 15: Messaging and Queuing System in OpenStack
OpenStack Series Part 16: Ceph in OpenStack
OpenStack Series Part 17: Congress - Policy Service
OpenStack Series Part 18: Network Function Virtualization in OpenStack
OpenStack Series Part 19: Storage Polices for Object Storage
OpenStack Series Part 20: Group-based Policy for Neutron
Reference:
"Chapter 2. Identity Management." Document ATOM. N.p., n.d. Web. 03 Nov. 2014.
"Discover OpenStack: The Identity Component Keystone." Discover OpenStack: The Identity Component Keystone. N.p., n.d. Web. 03 Nov. 2014.
"Keystone/Federation/Blueprint." - OpenStack. N.p., n.d. Web. 03 Nov. 2014.

This comment has been removed by the author.
ReplyDeleteThank you for your thoughts.. its very useful to update my knoeledge DevOps training in chennai
ReplyDelete
ReplyDeleteThe blog you have shared is more informative... Thanks for your valid blog.
Selenium Training in Bangalore
Selenium Training in Coimbatore
Best Selenium Training Institute in Bangalore
best selenium training in coimbatore
RPA training in bangalore
Selenium Training in Bangalore
Java Training in Madurai
Oracle Training in Coimbatore
PHP Training in Coimbatore
Thank you for your articles that you have shared with us. Hopefully you can give the article a good benefit to us. Token Provider
ReplyDeleteThank's for sharing the useful information! . oracle training in chennai
ReplyDeleteI really appreciate your work and very amazing and important information
ReplyDeleteby cognex is the AWS Training in chennai